

Upgrade to D10 for Security
Upgrading to Drupal 10 before November 1st will guarantee that your website will be covered by new security update releases.
Drupal 10 has specific requirements to ensure ongoing security updates. It requires at least PHP 8.1 and Symfony 6. This choice is made to align with the end-of-life schedules of Symfony 4 (November 1st, 2023) and PHP 8.0 (November 26th, 2023). By adhering to these specified versions, Drupal 10 ensures an optimal support timeline, even though it already supports PHP 8.2.
If not upgraded to D10, your website will continue to run on Drupal 9 after November 1st, however, when Drupal core maintainers release a new version with security updates, your website will not be covered by these updates, leaving it vulnerable to attacks.
Example Attack
There are many kinds of attacks. Below is one example of a past security update which was released to prevent XSS attacks:
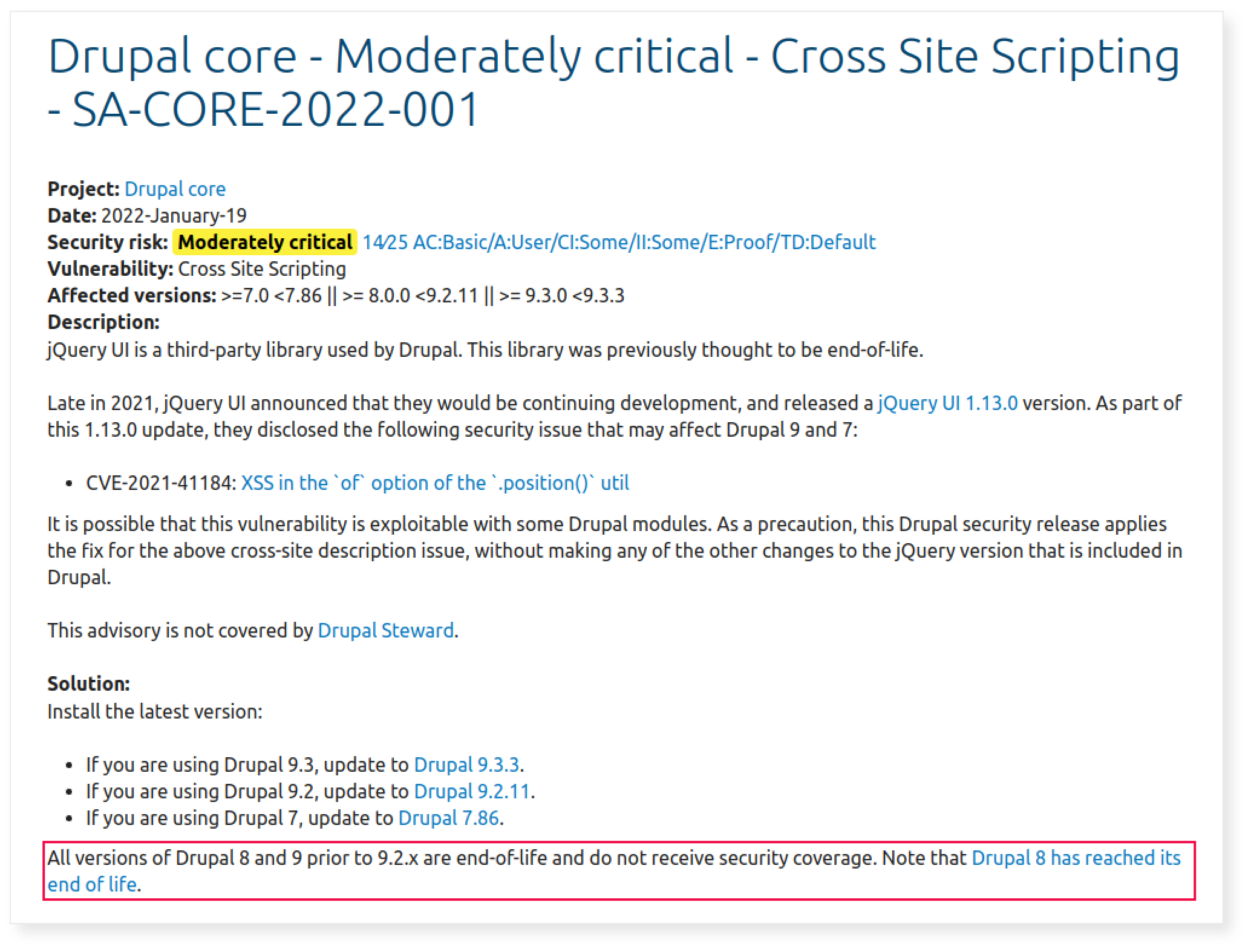
Example: Drupal 8 end of life was November 17, 2021. On January 19, 2022, the Drupal security team released a new minor version of Drupal 9 to apply a fix. So all Drupal 8 sites were left exposed to exploitation of this security vulnerability. A screenshot of this example is below.
This kind of XSS vulnerability might allow injection attacks using a web application to send malicious code, generally in the form of a browser-side script, to a different end user.
An attacker can use XSS to send a malicious script to an unsuspecting user. These malicious scripts can access any cookies, session tokens, or other sensitive information retained by the browser and used with that site.
Other Types of Attacks
There are many kinds of attacks that can happen on a Drupal application if it is not kept properly up to date, here are a few more examples:
SQL Injection
An SQL injection attack consists of the insertion of a Database code script via the input data from the client to the application. A successful SQL injection exploit can read sensitive data from the database, or modify database data (Insert/Update/Delete).
Directory Traversal
A path traversal attack (also known as directory traversal) aims to access files and directories that are stored outside the web root folder. It may be possible to access arbitrary files and directories stored on the file system including application source code or configuration and critical system files.
Input Validation
The application receives input or data, but it does not validate or incorrectly validate that the input has the properties that are required to process the data safely and correctly.
Denial of Service
The Denial of Service (DoS) attack is focused on making a resource (site, application, server) unavailable for the purpose it was designed.
Bypass
The application does not restrict, or incorrectly restrict, access to a resource from an unauthorized user.
As you can see, leaving your site vulnerable puts you at risk of experiencing:
- Site instability or outages.
- Spam users getting created, or spam form submission.
- Hacking and stealing of user account information.
- Content on your site is being deleted or changed.
- Blocking users from accessing their accounts or content.
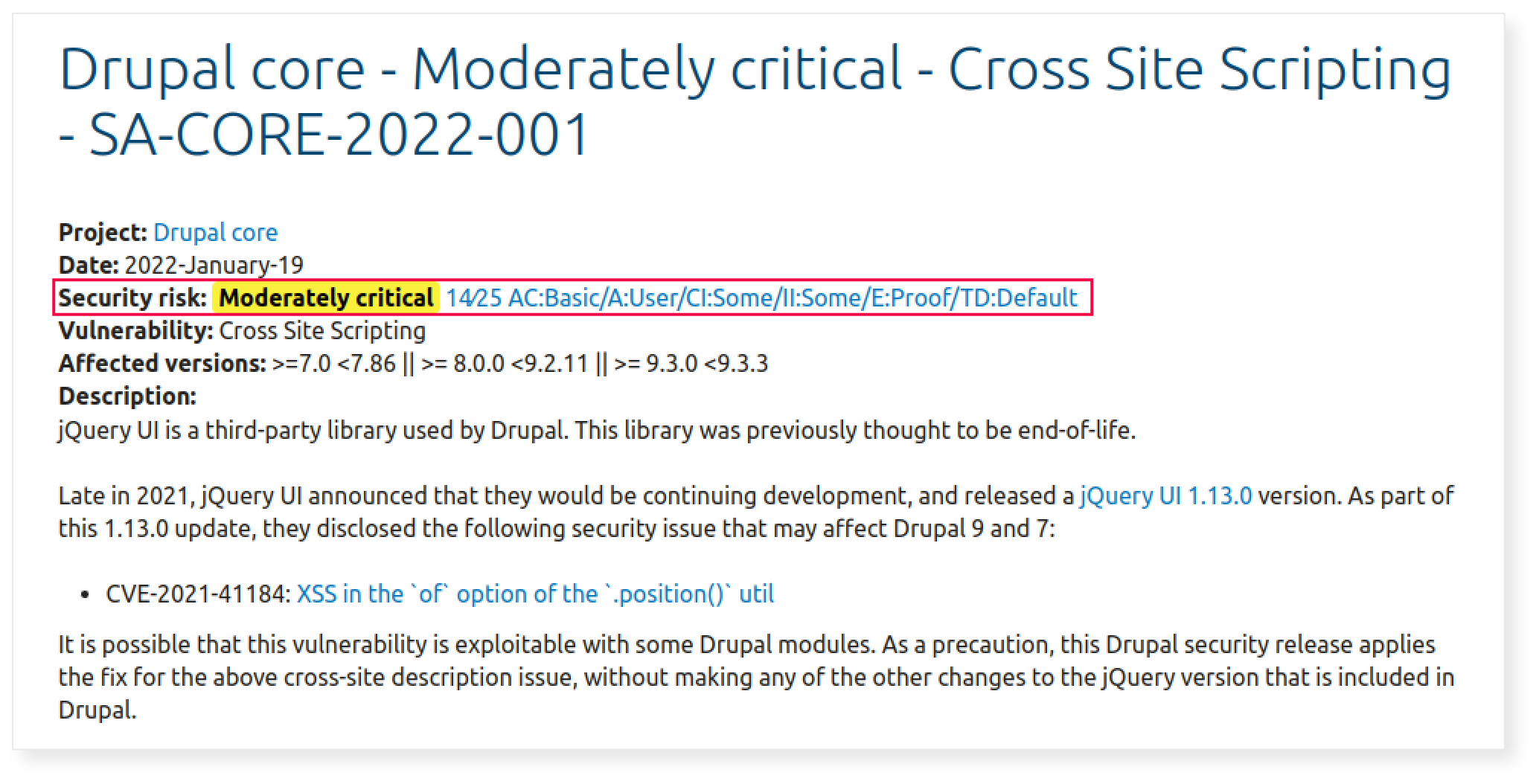
Risk Levels
It’s important to point out that each vulnerability is classified by the Security risk levels. This shows the level of risk of this vulnerability and the impact it can have on the Drupal application.
Frequency of Security Releases
Drupal Core maintainers release a minor version update approximately every six months, but in rare cases, an unscheduled minor version will be released in between. This is when a particularly severe bug fix is too disruptive for a patch version, but cannot wait until the next scheduled minor version update. The unscheduled minor version will include that one change by itself.
Below are some charts explaining the number of security releases for just Drupal Core alone, over the past years.
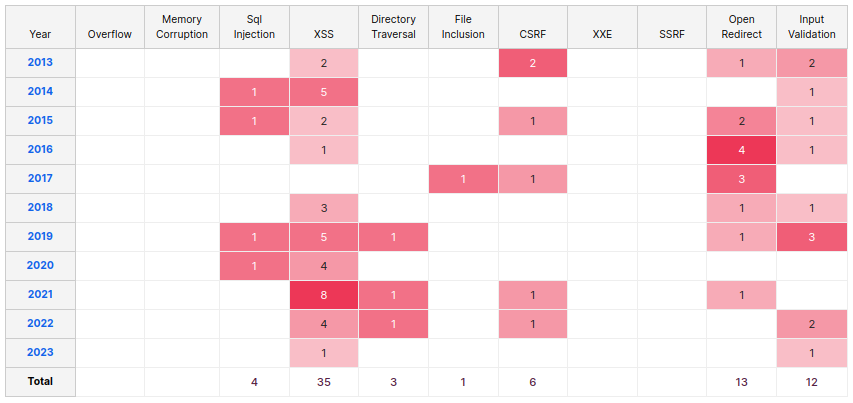
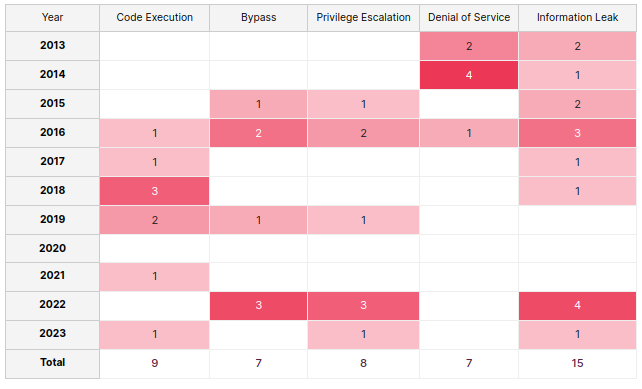
Drupal Core is just the central code for Drupal itself. Each site utilizes dozens of contributed modules that also need periodic security releases. This link shows a list of security advisories released for contributed modules: https://www.drupal.org/security/contrib. Depending on which modules your site uses, these can be fairly frequent. This is why our standard maintenance agreements involve updating Core and modules on a monthly rolling schedule. You can read more about our maintenance process here: https://www.twel.io/articles/twels-approach-drupal-security-maintenance
Not just Security, Stability too.
Also, general stability and performance can be affected by not keeping Drupal and all its modules up to date, because the modules might become vulnerable through incompatibilities with core or with one another if they are not all updated to an equal degree in a timely manner. Contact us for a free consultation about Drupal maintenance and tell us the challenges you are facing with your website.
References:
- https://www.drupal.org/about/core/policies/core-release-cycles/schedule
- https://www.drupal.org/about/core/policies/core-release-cycles/overview-of-the-release-process
- https://owasp.org/www-community/attacks
- https://www.drupal.org/drupal-security-team/security-risk-levels-defined
- https://www.cvedetails.com/product/2387/Drupal-Drupal.html?vendor_id=1367
- https://cwe.mitre.org/data/definitions/20.html